- Community Home
- Announcements
- Re: SIM Swap Fraud
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Subscribe
- Mute
- Printer Friendly Page
SIM Swap Fraud
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021
09:26 AM
- last edited on
07-14-2021
10:22 AM
by
J_PM
![]()
*July 14, 2021 Update*
We are pleased to announce that as of July 14, 2021, SIM card changes have been re-enabled in My Account.
We temporarily disabled all online SIM swaps in March, to protect our customers from SIM swap fraud.
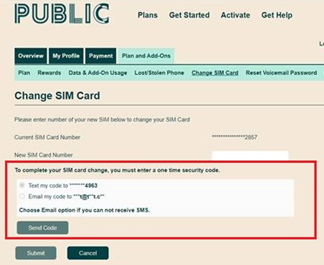
We have now implemented an additional step in the form of a 2 factor-authentication code to secure this process.This code can be sent via SMS or email, and must be verified to complete the SIM swap.
For more details, please see below.
All the information below can be found in this Help Article.
---------------------------------
*March 8, 2021 Update*
To protect our customers from SIM swap fraud, we have temporarily disabled all online SIM swaps through Self-serve. To change your SIM card, please submit a ticket here
Customer safety and security is our priority, and we are working on permanently securing the online SIM swap process. In the meantime, we recommend that you continue following the steps outlined below to protect against fraudulent activities.
-------------------------------
Hey Community,
We’ve noticed some cases of SIM swap fraud, and wanted to help our customers better understand what SIM swap fraud is, what to do if you’ve been targeted, and how to prevent it in the future.
All the information below can be found in this Help Article.
What is SIM swap fraud?
Efforts by fraudsters to gain unauthorized access to customer accounts with the goal of accessing banking information is on the rise. As part of our commitment to protect our customers’ personal information, we have robust security protocols in place that are designed to protect the privacy and security of our customers.
SIM swap fraud, or SIM jacking, is a type of fraud that occurs when fraudsters gain access to your Self Serve account, to replace your SIM card information with their own. After replacing your SIM card, all communications will be redirected to the fraudster’s device. They will then be able to intercept recovery SMS/calls, and gain access to your personal banking, ecommerce, email and social media accounts.
How does SIM swap fraud happen?
Fraudsters can obtain customer Self Serve account credentials through malware, phishing attempts or data breaches on websites where login credentials are the same as your Self Serve account.
What do I do if I’ve been targeted by SIM swap fraud?
If you have been targeted by SIM swap fraud, we recommend you take the following actions to secure your account:
- Change your Self-Serve account password and security question immediately to lock the fraudster out of your account
- Put your phone into Lost/Stolen mode to suspend the fraudster’s service, to do this follow the below steps:
- Log in to you Self-Serve account
- Go to Plans and Add-Ons, then select “lost/stolen phone”
- Select “suspend service”
- Then, submit a ticket here - our Moderator team will be able to restore your original SIM card.
- We also recommend contacting your financial institutions to ensure your banking and credit card accounts have not been accessed, and checking your social media accounts for any suspicious activity. Make sure you change your passwords to these accounts immediately.
- You may also want to report the fraud to your local police and the Canadian Anti-Fraud Centre at 1-888-495-8501, as well as contact the two national credit bureaus to request a copy of your credit reports and place a fraud warning on your file (Equifax Canada Toll free:1-800-465-7166 and TransUnion Canada Toll free: 1-877-525-3823).
How to protect against SIM swap fraud?
Given the increase the telecommunications industry has seen in fraudulent activity like SIM swaps and unauthorized porting, we recommend that Canadians take the following steps to protect themselves:
- Protect your information: limit the amount of personal information about you online; fraudsters can use this information to verify your identity when attempting to swap your SIM. Be careful to not click on phishing emails (and texts) that ask you to provide and/or validate private information.
- Guard your phone number: don’t add your phone number to any online accounts where it is not necessary. The fewer accounts you have associated with your number, the lesser your risk.
- Use strong and unique passwords for each of your accounts: using the same password across multiple accounts is a hacker’s jackpot. When you use the same password across different accounts, remember that once they successfully hack one account, they’ve hacked them all. We also recommend that you change your passwords, including your Self-Serve password regularly.
- Set up authentication methods that aren’t text based: often, online accounts will require you to set up two-factor-authentication (2FA) for added protection; with 2FA, you need to authenticate yourself with something in addition to your username and password, such as a code that is sent to your device by text. With SIM swap fraud on the rise, you may want to use something other than your phone number for 2FA like an authenticator app or security key.
While Public Mobile is actively working on ways to help keep our customers safe, please make sure to stay vigilant, and be aware of any suspicious activity.
- The Public Mobile Team
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2021 01:46 PM
Agree @Korth What was the intent of Frank1's initial question?
Lot's of critiques of Public Mobile's systems (which are FAR from perfect) but little feedback otherwise. Would be really helpful if he might simply share what had happened and what FIXED his issue.
Maybe what upset him so much didn't turn out to be the problem after all???
Oh well, easy come, easy go.... 🙄
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2021 01:21 PM
@Frank1 wrote:I'll just get a google voice number.
...
No 2FA at all? Seriously? What a compete joke.
Google Voice is just layered onto another phone service - one which requires an active phone number, and (if mobile) an active SIM card. So how exactly is it supposed to prevent or recover from a SIM swap?
2FA through the phone number isn't a good idea when the phone number itself is the target of the crime. The 2FA would in fact make it harder for the legit owner (who has lost access to the phone number) to confirm identity while making it easier for the thief (who is using the stolen phone number) to spoof or change this identity.
Need constructive suggestions, not idealistic buzzwords. The whole basis of "2FA" security is to use a separate channel. You shouldn't secure your phone number with your phone number the same way you shouldn't use an anonymous mailing address which is the same as your real address.
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2021 02:26 PM
Can you share a little bit more about what happened to your service yesterday? Were you SIM jacked?
Were the moderators able to fill you in on what occurred?
The community would like to know to learn from the experience.
Thank you!!!
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 09:35 PM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 07:53 PM
@?
Lol...nice tag!
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 07:51 PM - edited 04-05-2021 07:52 PM
@Frank1 it's a cheap provider... what do you expect? it is what it is... I'm sure your issue is just the system maintenance public was doing today.
the best pm has done to secure our accounts is the removal of the change sim feature. and since then I haven't seen a post yet on sim swaps. I'm assuming mods know which accounts were data breached and are able to make better judgement calls.
I'm also wondering if they forced certain accounts to deactivate the password so that the perpetrator isn't able to log in to the account to see personal details and such. then the real account holder needs to contact mods to verify their details to have their password changed
It's 20 minutes past 4:20 do you feel better now?
i do 😑🤣
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 07:41 PM
It's 20 minutes past 4:20 do you feel better now?
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 07:35 PM - edited 04-05-2021 07:36 PM
Already did all that and DMing with a mod.
@crustylady since you're a community expert here, how do I block annoying trolls with nothing better to do than to continuously annoy telco customers online?
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 07:27 PM
I doubt the user will ever get to the bottom of it, it seems from the content of the initial post they may already be near it.
Some people want to be helped - some really don't.
Which do you think this person is?
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 07:02 PM
@Frank1 wrote:I got service back. IDL what happened but I'll be damned if I don't get to the bottom of it.
You know sim swaps are a huge issue yet you don't offer either TOTP or hardware security key 2FA for swapping SIMs? Enjoy the lawsuits.
So incredibly irresponsible and stupid to say you need a long random password then only allow 20 characters and REQUIRE numbers/capitals. This disgusting practise is brought to you by 1 study in the 80s. Great. So based on absolutely nothing.
Want to know more? https://www.usatoday.com/story/news/nation-now/2017/08/09/password-expert-says-he-wrong-numbers-capi...
Here's an expert:
The man behind the 2003 report responsible for many current password guidelines says the advice is wrong.
Bill Burr, the author of an 8-page publication released by the National Institute of Standards and Technology, told The Wall Street Journal his previous advice of creating passwords with special characters, mixed-case letters and numbers won't deter hackers. In fact, he told the journal, the paper wasn't based on any real-world password data, but rather a paper written in the 1980s.
LONG passwords are key. RANDOM passwords are also key. Brute forcing Apple1 takes a fraction of a second but brute forcing aliplyRWEOYF92531 would take exponentially longer (like hundreds if not thousands of years - assuming no quantum computer).
What you think is a good password: HenryWinkler123!
What a real good password looks like: wink%taller%printer%flail
For those that don't have a clue how to make a password, here's a great website: https://www.correcthorsebatterystaple.net/
Now some mod email me ASAP. I have service again but need to know why it dropped out for an hour or more.
@Frank1 , sounds frustrating what you are/have experienced. I hope you get to the bottom of it; and keep us posted if you do. It will only help others.
Moderators don't reach out to customers. You need to reach out to them.
To contact the Public Mobile Moderator_Team, there are two ways to reach them:
1 - Faster Method - Click the bubble comment circle on the bottom right hand side of your screen, or use this link to: Get Help With SIMon the Public Mobile chatbot
OR
2 – Slower Method - Use this link to:
Private Message to Public Mobile Moderators (PM Customer Service Representatives)
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 06:32 PM
Hilarious. Ad hominem attacks. Thanks keyboard warrior.
The fact that the first time I see anything about sim swap attacks happening here is on your obscure forum that nobody reads is ridiculous.
I'll just get a google voice number. It's hard as hell as a Canadian but this BS is getting ridiculous and our masters of oligopoly Telus/Rogers/Bell don't give a crap about security.
No 2FA at all? Seriously? What a compete joke.
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 06:12 PM
Gee Frank, wouldn't it be funny if the cause of this potential outage was an accident or lightning strike or something.
I hear God has a pretty good lawyer, so you're in for a fun court battle.
LOL
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 05:56 PM
@Frank1 so your service just came back without the mod even get back to you? there was a Telus outage today.. any chance it is because of that instead?
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 05:44 PM
I got service back. IDL what happened but I'll be damned if I don't get to the bottom of it.
You know sim swaps are a huge issue yet you don't offer either TOTP or hardware security key 2FA for swapping SIMs? Enjoy the lawsuits.
So incredibly irresponsible and stupid to say you need a long random password then only allow 20 characters and REQUIRE numbers/capitals. This disgusting practise is brought to you by 1 study in the 80s. Great. So based on absolutely nothing.
Want to know more? https://www.usatoday.com/story/news/nation-now/2017/08/09/password-expert-says-he-wrong-numbers-capi...
Here's an expert:
The man behind the 2003 report responsible for many current password guidelines says the advice is wrong.
Bill Burr, the author of an 8-page publication released by the National Institute of Standards and Technology, told The Wall Street Journal his previous advice of creating passwords with special characters, mixed-case letters and numbers won't deter hackers. In fact, he told the journal, the paper wasn't based on any real-world password data, but rather a paper written in the 1980s.
LONG passwords are key. RANDOM passwords are also key. Brute forcing Apple1 takes a fraction of a second but brute forcing aliplyRWEOYF92531 would take exponentially longer (like hundreds if not thousands of years - assuming no quantum computer).
What you think is a good password: HenryWinkler123!
What a real good password looks like: wink%taller%printer%flail
For those that don't have a clue how to make a password, here's a great website: https://www.correcthorsebatterystaple.net/
Now some mod email me ASAP. I have service again but need to know why it dropped out for an hour or more.
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2021 05:14 PM - edited 04-05-2021 06:44 PM
I'm likely a victim. Someone reach out asap.
I take my security very seriously and not even offering 2FA this day and age is a complete and utter joke. I'm sure our passwords and therefore names/addresses have been leaked. We're all screwed.
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2021 08:10 PM
Thanks, i agree always use a strong password, do not recycle password or use same password on multiple sites and if 2FA/MFA option is available always use it.
for authenticator app i recommend Authy. 🙂
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2021 01:16 AM - edited 03-20-2021 01:17 AM
Sorry to hear about losing your phone. Have you suspended your service by using the lost/stolen feature in your account? You will still be able to retrieve your voicemail by dialing your number then when it connects press "*" and enter your 4 digit pin code.
When you get in contact with the moderator to change your sim card they will ask you to verify that you are the account holder by asking you additional identifiers. Be prepared by having the ability to answer most of the following that you could be asked to supply to the moderator.....
- Full name and address /or province and postal code on your account.
- Email, pin # and phone #.
If you don't remember your pin # include at least 3 of the following:
- Last payment, amount, date, type and last 4 digits.
- Alternate phone # if any.
- Date of birth.(n/a on new accounts)
- Plan amount, recent changes, any add ons on account.
- Security question and answer.
- Frequently called/texted numbers.
- Activation date.
- Last 4 digits of your sim card.
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2021 12:59 AM - edited 03-20-2021 12:59 AM
@prayerful wrote:I have lost my cell phone. please help me to transfer info to new sim card
for transferring new SIM Card, did you get one yet? the quickest way is to get it from local Kiosk like Walmar/Loblaws/London Drug or online from Amazon for Prime Delivery.
Once you got the SIM, you can request swap SIM to work with MOD at this link
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2021 12:56 AM
I have lost my cell phone. please help me to transfer info to new sim card
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2021 12:53 AM - edited 03-20-2021 01:02 AM
@prayerful wrote:I lost my cell phone and I would love to get my contact info., messages, and phone calls
You should first logon to Self-Serve, Plan Add-on Tab -> Lost/Stolen Phone and click Suspend Service
Your service will then suspend. Try to find the phone or get a replacement phone and SIM within 89 days or you will lost your number.
For contact info or message, if you have turned on Auto-backup, you might have luck from your Google or Apple cloud backup..
Good Luck!
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2021 12:47 AM
I lost my cell phone and I would love to get my contact info., messages, and phone calls
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2021 04:26 PM
I'm none too happy about this either but a 48 hour wait is rare and usually 2 to 4 hours and lately an hour or less....
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2021 03:34 PM
Well, it's not that so convenient. If my sim card is lost or damaged, i need wait very long to get my service back. On top of that, moderators may take 48 hours or longer to reply, and need me verify this and that. One time I forgot my pin code (which was generated randomly and I didn't wrote down).
For safety reason, I'm ok on that though.
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2021 08:20 PM
Glad to hear there’s at least something being done to help with this. I can’t tell if it’s more common with public mobile or if it’s because this is one of the few providers where other users actually discuss things with each other so we’d be more “in the know”.
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2021 02:29 PM - edited 03-11-2021 02:31 PM
If you haven't heard back from the moderators then something has gone wrong with your ticket. Use my preferred method of contact you should recieve a response within the hour...
To send a private message and include a detailed message explaining the issue. Then add the following.....
- Full name and address /or province and postal code on your account.
- Email, pin # and phone #.
If you don't remember your pin # include at least 3 of the following:
- Last payment, amount, date, type and last 4 digits.
- Alternate phone # if any.
- Date of birth.(n/a on new accounts)
- Plan amount, recent changes, any add ons on account.
- Security question and answer.
- Frequently called/texted numbers.
- Activation date.
- Last 4 digits of your sim card.
Keep an eye on the envelope icon next to your avatar at the top right corner of your screen for a little number to pop up indicating a message from the moderators. Responding promptly to messages will speed up service times. Wait times average 2 to 4 hours up to 48 hours for non urgent requests. Current wait times are about one hour or less. Ask for a review link if you would like to rate the customer service you have recieved.
To send a private message to the moderators click below:
https://productioncommunity.publicmobile.ca/t5/notes/composepage/note-to-user-id/22437
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2021 02:13 PM
@kyhustle : I can sympathize. Since they took away the ability to self-serve a SIM change, ostensibly for fraud avoidance to "protect" their customers, this is the result. Sucks. Poor response doesn't help at all either. Wow. Can't blame ya.
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2021 02:10 PM
This is stupid. 48 HOURS to switch my sim card? I'll be switching providers. Some loser has my cellphone out there and yes of course I google locked him and sim locked him, but then I can't get a new sim setup? All day yesterday my tickets kept getting denied, even the **bleep** chatbot seemed rude. Public Mobile NEEDS to step away from this community based support or atleast have a small call center to deal with issues like this. I've been without my phone for about a week now and now I need to wait up to 48 hours for them to finalize the switch? NOT IMPRESSED. I'm looking into VOIP options and other options aswell. Like ugh
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2021 12:01 PM
Every11S2ea$E24get?
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2021 11:24 AM
@darlicious wrote:Good sound advice. Coming from a very much non-IT background I'm just highly internet suspicious and online paranoid. And old fashioned.....so rather than a password manager I use write them down and hide them well method of saving my passwords along with memorization only for a few very important passwords like my bank and google/email accounts. I have a convoluted system that serves me well.
@darlicious Whatever works for you is OK and you should be suspicious. As long as you don't use the same password (or too easy to guess) for your all logins you should be generally ok.. There are sites to check your password strength.
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2021 10:50 AM
Good sound advice. Coming from a very much non-IT background I'm just highly internet suspicious and online paranoid. And old fashioned.....so rather than a password manager I use write them down and hide them well method of saving my passwords along with memorization only for a few very important passwords like my bank and google/email accounts. I have a convoluted system that serves me well.
- eSIM Cost: How Often Can It Be Downloaded? What Happens if I Swap Phones Often? in Get Support
- How to swap esim for sim card? in Get Support
- Resume activation request when I did not buy new SIM card - How to cancel without service impact in Get Support
- Getting my phone number back to Public in Get Support
- Refunding this new subscription and sim card in Get Support